About Dependabot
This quickstart guide walks you through setting up and enabling Dependabot, viewing Dependabot alerts, and updating your repository to use a secure version of the dependency.
O Dependabot consiste em três recursos diferentes que ajudam você a gerenciar dependências:
- Dependabot alerts: informam você sobre vulnerabilidades nas dependências usadas em um repositório.
- Dependabot security updates: geram automaticamente pull requests para atualizar as dependências usadas que possuem vulnerabilidades de segurança conhecidas.
- Dependabot version updates: geram automaticamente pull requests para manter suas dependências atualizadas.
Prerequisites
For the purpose of this guide, we're going to use a demo repository to illustrate how Dependabot finds vulnerabilities in dependencies, where you can see Dependabot alerts on GitHub, and how you can explore, fix, or dismiss these alerts.
You need to start by forking the demo repository.
- Navigate to https://github.com/dependabot/demo.
- At the top of the page, on the right, click Fork.
- Select an owner (you can select your GitHub personal account) and type a repository name. For more information about forking repositories, see Criar fork de um repositório.
- Click Create fork.
Enabling Dependabot for your repository
You need to follow the steps below on the repository you forked in Prerequisites.
-
Em GitHub, acesse a página principal do repositório.
-
No nome do repositório, clique em Settings. Caso não consiga ver a guia "Configurações", selecione o menu suspenso , clique em Configurações.
-
Na seção "Security" da barra lateral, clique em Advanced Security.
-
Under "Dependabot", click Enable for Dependabot alerts, Dependabot security updates, and Dependabot version updates.
-
If you clicked Enable for Dependabot version updates, you can edit the default
dependabot.ymlconfiguration file that GitHub creates for you in the/.githubdirectory of your repository. To enable Dependabot version updates for your repository, you typically configure this file to suit your needs by editing the default file, and committing your changes. You can refer to the snippet provided in Configuração de atualizações de versão do Dependabot for an example.
Observação
If the dependency graph is not already enabled for the repository, GitHub will enable it automatically when you enable Dependabot.
For more information about configuring each of these Dependabot features, see Configurando alertas do Dependabot, Configuração de atualizações de segurança do Dependabot, and Configuração de atualizações de versão do Dependabot.
Viewing Dependabot alerts for your repository
If Dependabot alerts are enabled for a repository, you can view Dependabot alerts on the "Security" tab for the repository. You can use the forked repository that you enabled Dependabot alerts on in the previous section.
-
Em GitHub, acesse a página principal do repositório.
-
Abaixo do nome do repositório, clique em Security. Caso não consiga ver a guia "Security", selecione o menu suspenso e clique em Security.

-
Na barra lateral "Alertas de vulnerabilidade" da visão geral de segurança, clique em Dependabot . Se essa opção está ausente, isso significa que você não tem acesso aos alertas de segurança e precisa receber o acesso. Para obter mais informações, confira Gerenciando as configurações de segurança e análise do repositório.
-
Review the open alerts on the Dependabot alerts page. By default, the page displays the Open tab, listing the open alerts. (You'll be able to view any closed alerts by clicking Closed.)
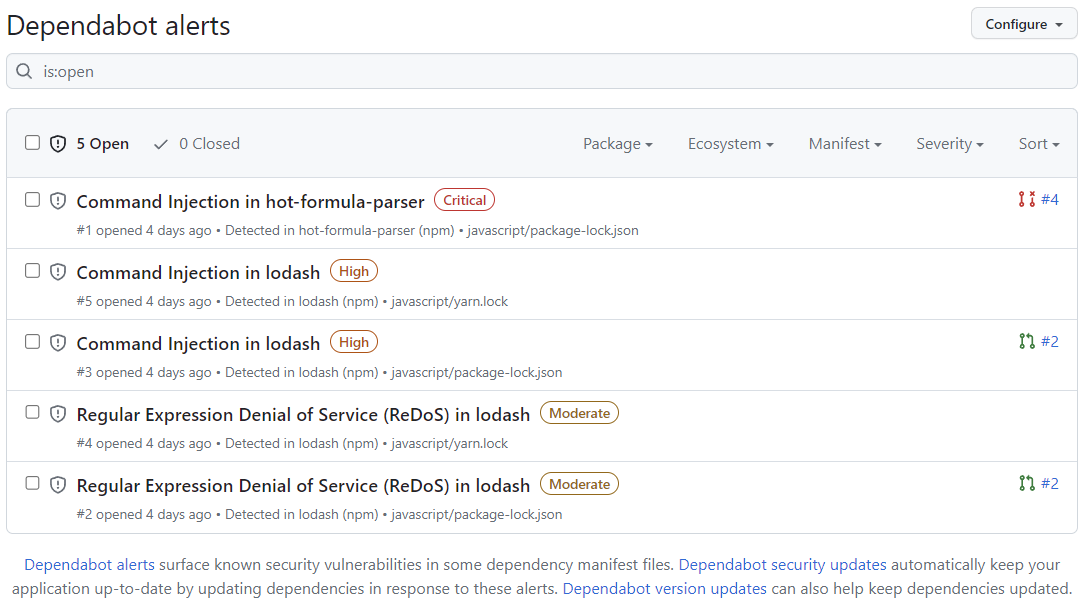
You can filter Dependabot alerts in the list, using a variety of filters or labels. For more information, see Visualizando e atualizando alertas do Dependabot. You can also use Regras de triagem automática do Dependabot to filter out false positive alerts or alerts you're not interested in. For more information, see Sobre as regras de triagem automática do Dependabot.
-
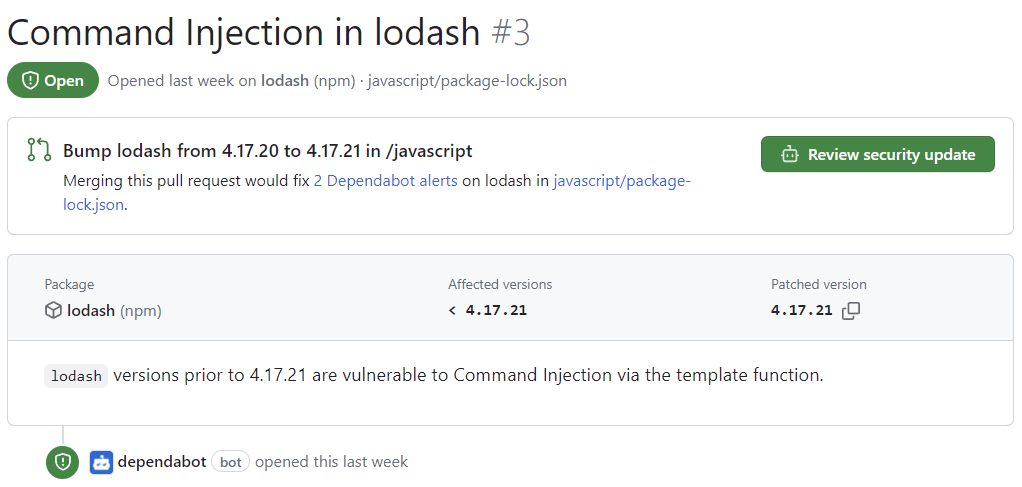
Click the "Command Injection in lodash" alert on the
javascript/package-lock.jsonfile. The details page for the alert will show the following information (note that some information may not apply to all alerts):- Whether Dependabot created a pull request that will fix the vulnerability. You can review the suggested security update by clicking Review security update.
- Package involved
- Affected versions
- Patched version
- Brief description of the vulnerability
-
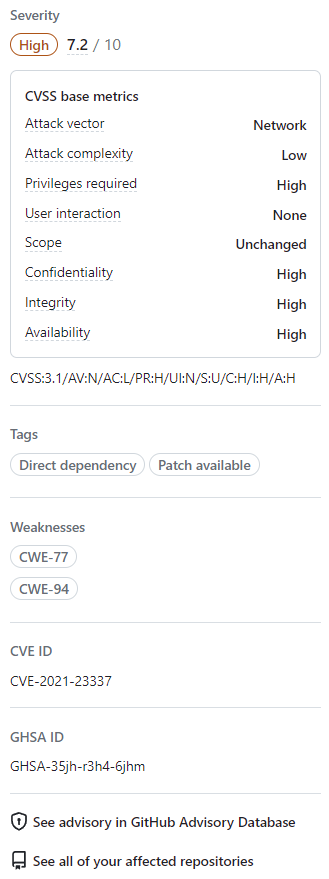
Optionally, you can also explore the information on the right-side of the page. Some of the information shown in the screenshot may not apply to every alert.
- Severity
- CVSS metrics: We use CVSS levels to assign severity levels. For more information, see Sobre o banco de dados de avisos do GitHub.
- Tags
- Weaknesses: List of CWEs related to the vulnerability, if applicable
- CVE ID: Unique CVE identifier for the vulnerability, if applicable
- GHSA ID: Unique identifier of the corresponding advisory on the GitHub Advisory Database. For more information, see Sobre o banco de dados de avisos do GitHub.
- Option to navigate to the advisory on the GitHub Advisory Database
- Option to see all of your repositories that are affected by this vulnerability
- Option to suggest improvements for this advisory on the GitHub Advisory Database
For more information about viewing, prioritizing, and sorting Dependabot alerts, see Visualizando e atualizando alertas do Dependabot.
Fixing or dismissing a Dependabot alert
You can fix or dismiss Dependabot alerts on GitHub. Let's continue to use the forked repository as an example, and the "Command Injection in lodash" alert described in the previous section.
- Navigate to the Dependabot alerts tab for the repository. For more information, see the Viewing Dependabot alerts for your repository section above.
- Click an alert.
- Click the "Command Injection in lodash" alert on the
javascript/package-lock.jsonfile. - Review the alert. You can:
-
Review the suggested security update by clicking Review security update. This will open the pull request generated by Dependabot with the security fix.
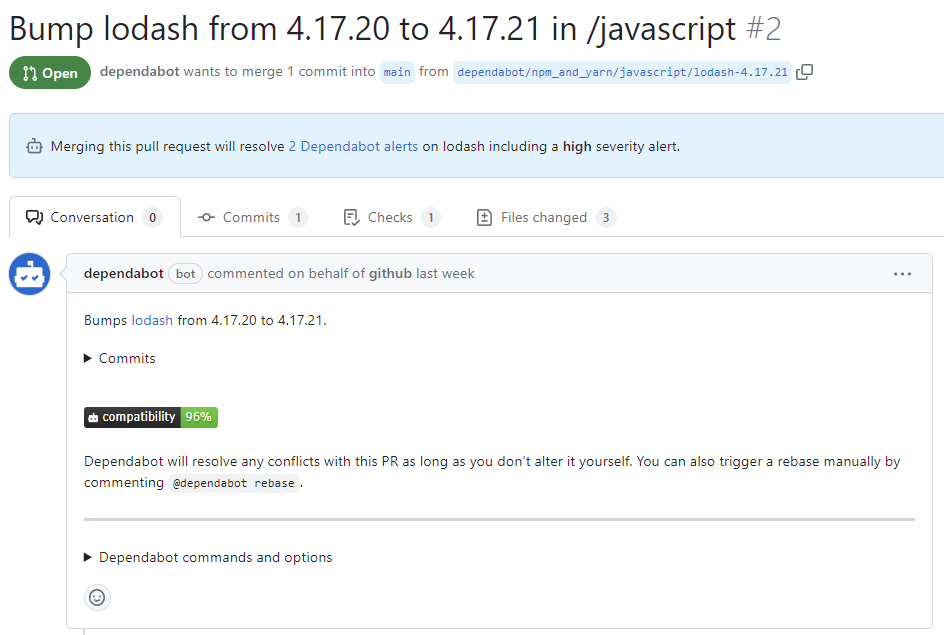
- On the pull request description, you can click Commits to explore the commits included in the pull request.
- You can also click Dependabot commands and options to learn about the commands that you can use to interact with the pull request.
- When you're ready to update your dependency and resolve the vulnerability, merge the pull request.
-
If you decide that you want to dismiss the alert
-
Go back to the alert details page.
-
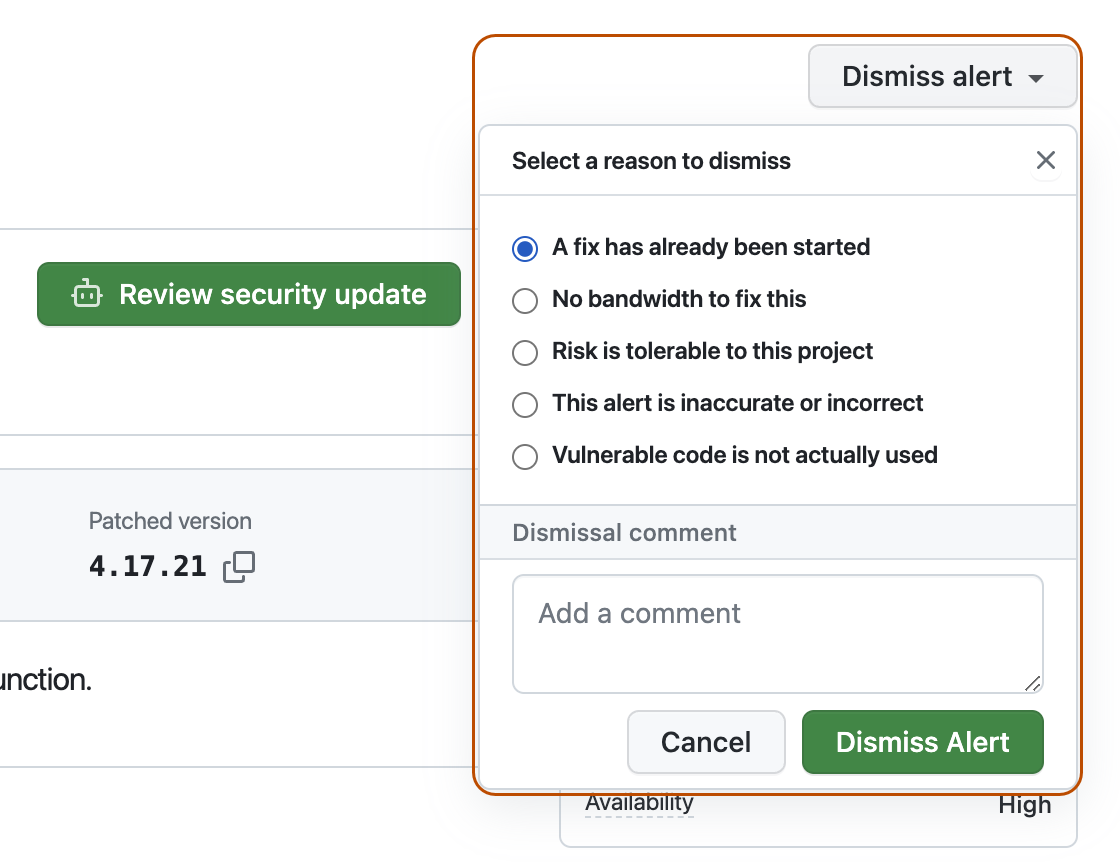
On the top-right corner, click Dismiss alert.
-
Select a reason for dismissing the alert.
-
Optionally, add a dismissal comment. The dismissal comment will be added to the alert timeline and can be used as justification during auditing and reporting.
-
Click Dismiss alert. The alert won't appear anymore in the Open tab of the alert list, and you are able to view it in the Closed tab.
-
-
For more information about reviewing and updating Dependabot alerts, see Visualizando e atualizando alertas do Dependabot.
Troubleshooting
You may need to do some troubleshooting if:
- Dependabot is blocked from creating a pull request to fix an alert, or
- The information reported by Dependabot is not what you expect.
For more information, see Solução de problemas do Dependabot and Solução de problemas de detecção de dependências vulneráveis, respectively.
Next steps
For more information about configuring Dependabot updates, see Configuração de atualizações de segurança do Dependabot and Configuração de atualizações de versão do Dependabot.
For more information about configuring Dependabot for an organization, see Configurando alertas do Dependabot.
For more information about viewing pull requests opened by Dependabot, see Gerenciar pull requests para atualizações de dependências.
For more information about the security advisories that contribute to Dependabot alerts, see Como procurar avisos de segurança no GitHub Advisory Database.
For more information about configuring notifications about Dependabot alerts, see Configurando notificações para alertas do Dependabot.