About evaluating alerts
There are some additional features that can help you to evaluate alerts in order to better prioritize and manage them. You can:
- Check the validity of a secret, to see if the secret is still active. Applies to GitHub tokens only. See Checking a secret's validity.
- Perform an "on-demand" validity check, to get the most up to date validation status. See Performing an on-demand validity check.
- Review a token's metadata. Applies to GitHub tokens only. For example, to see when the token was last used. See Reviewing GitHub token metadata.
- Review extended metadata checks for an exposed secret, to see details such as who owns the secret and how to contact the secret owner. Applies to OpenAI API, Google OAuth, and Slack tokens only. See Reviewing extended metadata for a token.
- Review the labels assigned to the alert. For more information, see Reviewing alert labels.
Checking a secret's validity
Validity checks help you prioritize alerts by telling you which secrets are active or inactive. An active secret is one that could still be exploited, so these alerts should be reviewed and remediated as a priority.
By default, GitHub checks the validity of GitHub tokens and displays the validation status of the token in the alert view.
Organizations using GitHub Team or GitHub Enterprise Cloud with a license for GitHub Secret Protection can also enable validity checks for partner patterns. For more information, see Checking a secret's validity.
| 有效期 | Status | 结果 |
|---|---|---|
| 活动机密 | active | GitHub 向此机密的提供者进行了核实,发现此机密处于活动状态 |
| 可能处于活动状态的机密 | unknown | GitHub 尚不支持对此令牌类型进行验证检查 |
| 可能处于活动状态的机密 | unknown | GitHub 无法验证此机密 |
| 机密处于非活动状态 | inactive | 应确保未发生未经授权的访问 |
合作伙伴模式的有效性检查可用于以下存储库类型:
- 启用了 GitHub Secret Protection 的 GitHub Team 或 GitHub Enterprise Cloud 上的组织拥有的存储库
GHE.com 上的 具有数据驻留的 GitHub Enterprise Cloud 不支持针对合作伙伴模式的有效性检查。
For information on how to enable validity checks for partner patterns, see Enabling validity checks for your repository, and for information on which partner patterns are currently supported, see 支持的机密扫描模式.
You can use the REST API to retrieve a list of the most recent validation status for each of your tokens. For more information, see 适用于机密扫描的 REST API 终结点 in the REST API documentation. You can also use webhooks to be notified of activity relating to a secret scanning alert. For more information, see the secret_scanning_alert event in Webhook 事件和有效负载.
Asking GitHub Copilot 聊天 about secret scanning alerts
With a GitHub Copilot Enterprise license, you can ask Copilot 对话助手 for help to better understand security alerts, including secret scanning alerts, in repositories in your organization. For more information, see 在 GitHub 中向 GitHub Copilot 提问.
Performing an on-demand validity check
Once you have enabled validity checks for partner patterns for your repository, you can perform an "on-demand" validity check for any supported secret by clicking Verify secret in the alert view. GitHub will send the pattern to the relevant partner and display the validation status of the secret in the alert view.
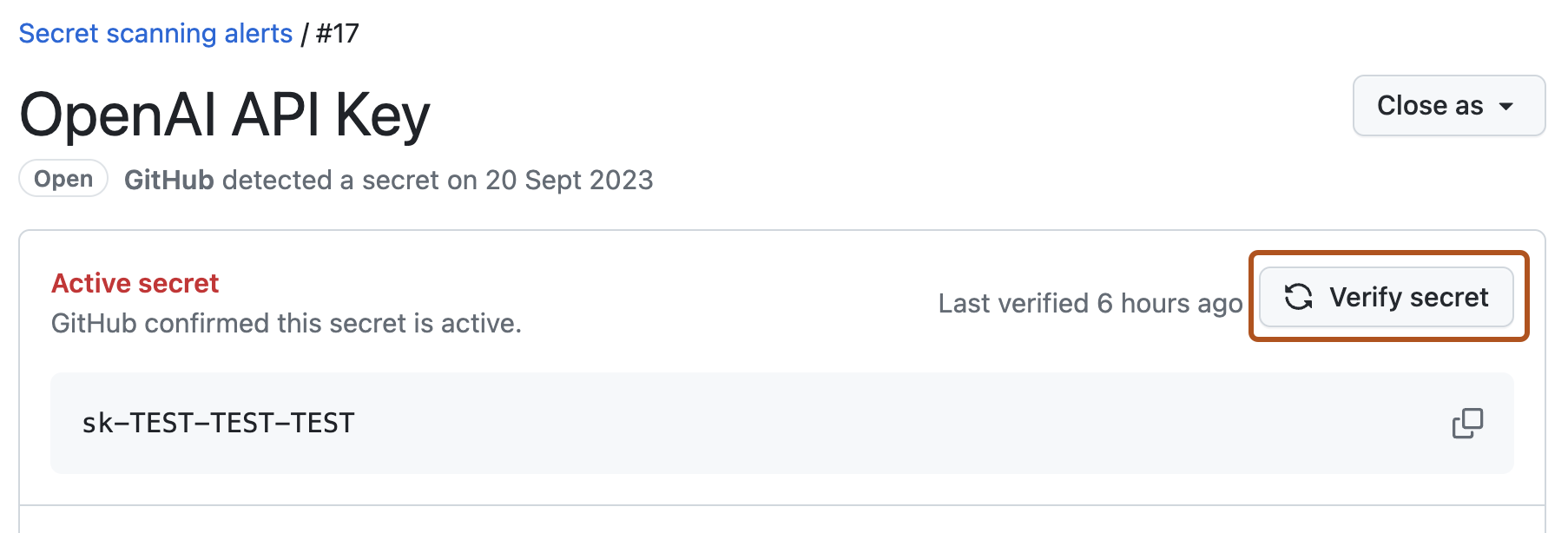
Reviewing GitHub token metadata
注意
Metadata for GitHub tokens is currently in 公共预览版 and subject to change.
In the view for an active GitHub token alert, you can review certain metadata about the token. This metadata may help you identify the token and decide what remediation steps to take.
Tokens, like personal access token and other credentials, are considered personal information. For more information about using GitHub tokens, see GitHub's Privacy Statement and Acceptable Use Policies.
Metadata for GitHub tokens is available for active tokens in any repository with secret scanning enabled. If a token has been revoked or its status cannot be validated, metadata will not be available. GitHub auto-revokes GitHub tokens in public repositories, so metadata for GitHub tokens in public repositories is unlikely to be available. The following metadata is available for active GitHub tokens:
| Metadata | Description |
|---|---|
| Secret name | The name given to the GitHub token by its creator |
| Secret owner | The GitHub handle of the token's owner |
| Created on | Date the token was created |
| Expired on | Date the token expired |
| Last used on | Date the token was last used |
| Access | Whether the token has organization access |
只有对包含已泄露机密的存储库具有管理员权限的人员才能查看安全警报详细信息和警报的令牌元数据。 企业所有者可以出于此目的请求对存储库的临时访问权限。 If access is granted, GitHub will notify the owner of the repository containing the leaked secret, report the action in the repository owner and enterprise audit logs, and enable access for 2 hours. For more information, see 访问企业中用户拥有的存储库.
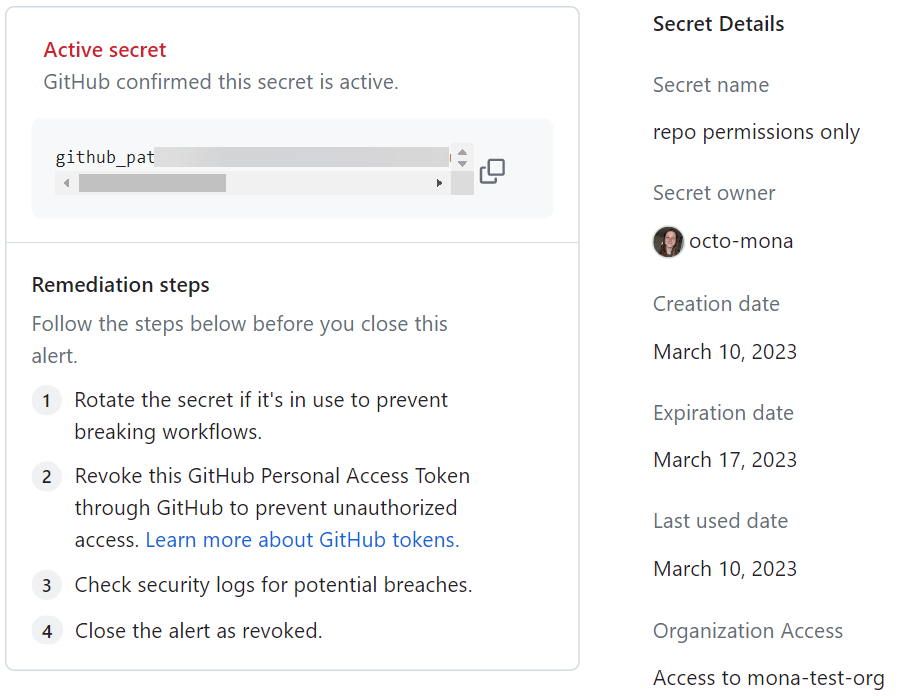
Reviewing extended metadata for a token
注意
扩展的令牌元数据检查功能处于公开预览中,并可能发生变化。
In the view for an active GitHub token alert, you can see extended metadata information, such as owner and contact details.
The following table shows all the available metadata. Note that metadata checks are currently limited to OpenAI API, Google OAuth, and Slack tokens, and the metadata shown for each token may represent only a subset of what exists.
| Metadata type | Description |
|---|---|
| Owner ID | Provider’s unique identifier for the user or service account that owns the secret |
| Owner name | Human‑readable username or display name of the secret’s owner |
| Owner email | Email address associated with the owner |
| Org name | Name of the organization / workspace / project the secret belongs to |
| Org ID | Provider’s unique identifier for that organization |
| Secret issued date | Timestamp when the secret (token or key) was created or most recently issued |
| Secret expiry date | Timestamp when the secret is scheduled to expire |
| Secret name | Human‑assigned display name or label for the secret |
| Secret ID | Provider’s unique identifier for the secret |
Reviewing alert labels
In the alert view, you can review any labels assigned to the alert. The labels provide additional details about the alert, which can inform the approach you take for remediation.
Secret scanning alerts can have the following labels assigned to them. Depending on the labels assigned, you'll see additional information in the alert view.
| Label | Description | Alert view information |
|---|---|---|
public leak | The secret detected in your repository has also been found as publicly leaked by at least one of GitHub's scans of code, discussions, gists, issues, pull requests, and wikis. This may require you to address the alert with greater urgency, or remediate the alert differently compared to a privately exposed token. | You'll see links to any specific public locations where the leaked secret has been detected. |
multi-repo | The secret detected in your repository has been found across multiple repositories in your organization or enterprise. This information may help you more easily dedupe the alert across your organization or enterprise. | If you have appropriate permissions, you'll see links to any specific alerts for the same secret in your organization or enterprise. |